I came across a cell phone the other day that had the Android pattern lock. This was a HTC EVO 4G, which is using the Sprint wireless network.
In order to gain access to the pattern locked device, I thought I would root the device. I checked to see if USB debugging was turned on by attempting to connect to the device using Adb.exe. It wasn’t..damn. Not too many options available at this point.
I had been reading up on the JTAG process from various posts. The actual soldering / JTAG process seemed to be the most difficult part of the process. I was only able to successfully complete this task after a good friend helped me get a clear picture of the overall process.
I bought my RIFF Box and assorted jigs from GSM Server. Yes, the parts came from Hong Kong. http://gsmserver.com/shop/gsm/riff_box_jtag.php
I purchased additional cell phone disassembly tools from Amazon.com and soldering equipment from my local MarVac Electronics store. I am ready to do this!!..so I thought.
Prior to soldering the wires to the HTC’s printed circuit board (PCB) test access port (TAP), I took apart other junk cell phones and attempted to hone my soldering skills. After ruining a couple of junk cell phone PCB’s along with some successful soldering attempts, I decided ‘I got this’.
My next course of self instruction was to watch a couple of HTC EVO 4G disassembly videos on YouTube. After watching about two or three 5 minute disassembly videos, I thought this is going to be a piece of cake!!
I was able to successfully disassemble the HTC EVO 4G down to the PCB.
If your soldering skillz need some work (like mine), this can be a long process. You need to connect/solder specific wires from the RIFF Box to the HTC’s JTAG TAP. This requires you to obtain documentation of the HTC’s JTAG pinout. Luckily, since RIFF Box supports the HTC EVO 4G (AKA: HTC Supersonic), the pinout diagram is included in the RIFF JTAG Management software. After a couple of hours, I was done soldering. YES!!
Now to connect all the parts so I can dump the HTC PCB’s NAND. I provided power to the HTC PCB using a Mastech Single-Output DC Power Supply, model# HY3003D. I connected my JTAG wiring from the HTC PCB to the RIFF Box. I next connected a USB cable from the computer to the microUSB slot on the HTC PCB. I connected the RIFF Box to the computer via USB and launched my RIFF JTAG software manager. I next turned on the HTC PCB. I knew the device was running because the Amp meter on my power supply was registered about a .10 amp draw.
With the RIFF JTAG software manager up and running, I selected the HTC Supersonic phone from the supported phone drop down menu. Next I selected the DCC Read/Write tab, then selected ‘Read Memory’. For all my hard work, I was presented with an error message that basically said the software was not talking to the phone. To make a long story short, after about an hour of trying to figure out what I did wrong, I discovered I soldered a wire to the wrong HTC PCB JTAG TAP. I attempted to de-solder the one wire. In the process, I de-soldered two adjacent wires. Great!!!! Another hour passed before I once again had all the wires soldered in their correct location. This time I was able to connect to the device and download the NAND. The one gigabyte download to over an hour to complete. Yah, the download crashed once or twice..Ok, a total of five times. But I was able to continue each time from where the process previously left off.
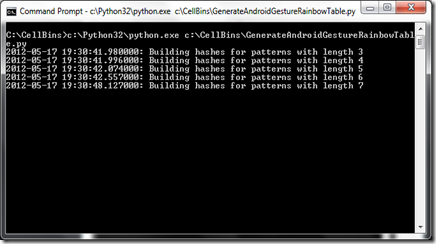
Using the Python3 GenerateAndroidGestureRainbowTable.py script from CCL Forensics (http://www.ccl-forensics.com/), I created the SHA1 rainbow table of hash values for pattern locks from 3 to 9 positions. The python script creates a rainbow table, storing the SHA1 hash values in a SQLite database. This might be a great time to take a break while the database is being created. The process took about 30 minutes to complete.
Once the script was finished, I was left with a SQLite database called ‘AndroidLockScreenRainbow.sqlite’. The SQLite database should be around 130MB in size.
My next step was to use the Android_GestureFinder.py python script from CCL Forensics. Basically this script will parse my HTC EVO NAND dump for the SHA1 pattern lock hash value. Once a hash value is located, the script will compare this hash value with the hash values stored in the AndroidLockScreenRainbow.sqlite database. When a SHA1 hash value match is located, the script will present you with the offset where the hash value was located within the NAND dump, the actual SHA1 hash value, and the pattern associated with the hash value. NOTE TO SELF: Make sure the Android_GestureFinder.py and the AndroidLockScreenRainbow.sqlite are in the same directory. If all goes well, you should get something like this…
Ok, so the pattern lock is 0, 3, 4, 1, 6 What does that mean?
Picture it this way:
I re-assembled the cell phone after de-soldering all my little wires. The device powered up and presented me with the ‘Draw pattern to unlock’. Drawing the above pattern, I was able to unlock the HTC EVO 4G. I immediately went into the Development settings and turned on USB Debugging, and Stay Awake.
From here, I can use whatever cell phone forensic software I have to download (physical or logical) the contents of the cell phone.
Hmmm. My next project just arrived. A PIN locked Samsung SPH-M820 cell phone on the Boost Mobile network…..




jtag starsat
ReplyDeletehttp://www.jtagg.com/forums
Excellent article and information, tool lists, photos, etc.
ReplyDeleteThank you very much!
Tim Mentzer
Can you share the JTAG pinout diagram?
ReplyDelete